RELEVANT: 1 Vulnhub Write-Up
Hey there! Today we are solving a new vulnhub boot2root challenge “RELEVENT: 1” create by “iamv1nc3nt”. It’s an intermediate box and here is the link below where you can download this box:- https://www.vulnhub.com/entry/relevant-1,568/
1.) Target Discovery
# netdiscover -i wlan0

We got the target Ip address which is 192.168.1.4
2.) Port Scanning and Service Detection
# nmap -sTV -p- -vv 192.168.1.4

From the above nmap scan we got two services running on the box which is ssh on port 22 and http on port 80.
3.) HTTP Enumeration
# dirb http://192.168.1.4/
I used dirb for simple directory brute-forcing and we got some wordpress directories on the box.

It means there is a wordpress installation on the box.
# wpscan — url http://192.168.1.4 -e ap — force
Remember that wpscan will not work on the box until you use — force option to force the wpscan to scan the target box.

And with the help of wpscan we got a vulnerable plugin “wp-file-manager” of version 6.7

we got the exploit of that plugin on the github. The vulnerability on the plugin allows an attacker to run commands which means Remote Code Execution (RCE).
After successfully exploiting the target box, time for POC
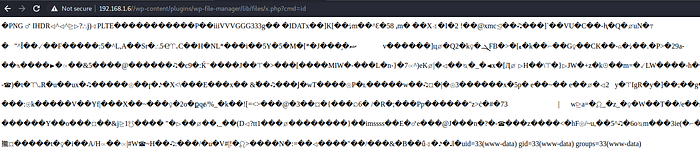
“http://192.168.1.4/wp-content/plugins/wp-file-manager/lib/files/x.php?cmd=id”
And we got the output back.
3.) Getting Reverse Shell
I started my listener on my localhost on port 1234 and got the reverse shell from that RCE.

4.) Privilege Escalation
After spending some time and some enumeration I found a directory named as “…” in the user h4x0r’s home directory.

In that “…” directory a text file was placed named as note.txt containing the credentials of the “news” user , but the password was encrypted in SHA-1 algorithm

So, I cracked that SHA-1 hash online and got the password which is “backdoorlover”

And yes we were able to switch user to news with that password.
now “# sudo -l” , With sudo command we can run “node” command with the root privileges.
# sudo node -e ‘require(“child_process”).spawn(“/bin/bash”,{stdio: [0, 1, 2]});’

With the help of node command we got the root shell and the root.txt flag also.

Challenge completed. !!! :)
