KIRA: CTF Write-Up
Hey there ! Today I have another boot2root ctf challenge KIRA:CTF on vulnhub and this ctf virtual machine is created by Bassam Assiri. Here is the link below where you can download this machine:-https://www.vulnhub.com/entry/kira-ctf,594/
1.)Target Discovery
# netdiscover -i wlan0

So, we got the target ip which is 192.168.1.7
2.) Port Scanning and Service Detection
For this job I used NMAP.
“# nmap -sT -p- -vv 192.168.1.7”

Here we have only open port 80 which is HTTP service.
3.) HTTP Enumeration

On the web, their are two buttons where one is to upload the picture on the server and another one is to choose the language for the server.

By clicking the language button I saw the possibility of Local File Inclusion (LFI) Vulnerability.

And yeh we have a LFI vulnerability on the server as you can see in the above image. We are able to view “/etc/passwd” file
Now its time for testing the file upload vulnerability.

I created a payload in php.php file as you can see in the image below. This payload will get a command from the “cmd” parameter.


Then in the burpsuite I changed the extension from “php.php” to “php.php.jpg” and the content-type header to image/jpeg.

And we successfully uploaded the payload. Now its time to check it. To trigger this payload I used LFI vulnerability.

And the payload is working, Now its time to get reverse shell from this payload.
4.) Capturing The Reverse Shell

After getting the reverse shell I saw a “supersecret-for-aziz” directory
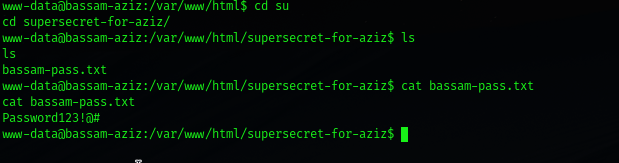
In That directory credentials for user “bassam” is stored ,so I switched the user to “bassam” with the provided credentials.


And we got the user flag.
5.) Privilege Escalation
“$ sudo -l”

We can run “find” command as user root without any password.

And after exploit the sudo rights we got the root access.

Here is the root flag “flag.txt”.
Challenge Completed !! :D
