BA: Mrr3b0t Vulnhub Write-Up
Hey There!!, Today I’m solving another boot2root challenge “bizarre adventure: mrr3b0t” created by “Joas Antonio” on vulnhub and here is the link below where you can downlaod this VM:-
“https://www.vulnhub.com/entry/bizarre-adventure-mrr3b0t,561/
1.) Target Discovery
# netdiscover -i wlan0
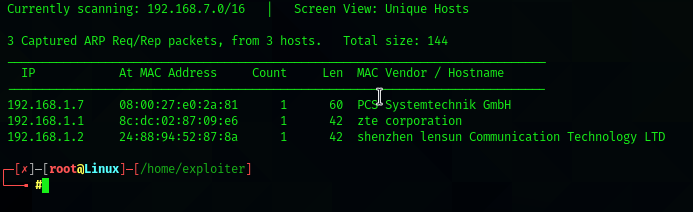
Here we have the ip address which is 192.168.1.7, Now its time for nmap scan
2.) Port Scanning and Version Detection
# nmap -sTV -p- 192.168.1.7

With the use of nmap we got few ports open on this VM ,so let’s start enumeration with port 80 which is http.
3.) HTTP Enumeration

Nothing interesting here, so for directory brute forcing I used gobuster and gobuster show an interesting directory “administrator”


After spending some time on the web I got “hidden.png” and “flag.txt.txt” files in the “images” directory
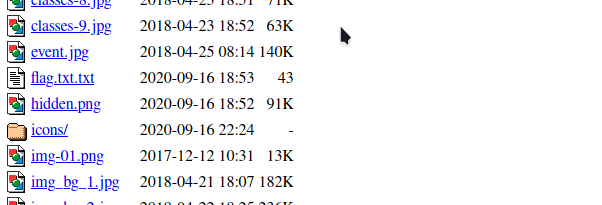
“flag.txt.txt” points towards the “hidden.png” image file
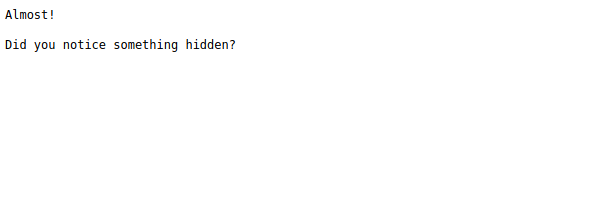

As flag is pointing towards the “hidden.png” file, so I tried for online steganography decoder to decode the message in the picture if any. Here is the link of that website for online steganography docder

And great!! we found something, so in this message we got our users to brute-force which is “mrrobot”
Then I brute-forced the credentials for the “administrator/index.php” login form and I got the correct cred.
“mrrobot:secret”

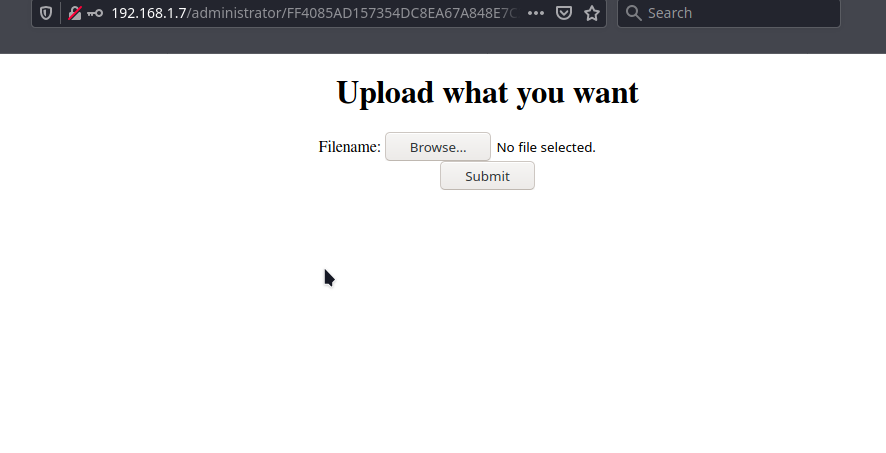
With the credentials we are successfully log in and here the page allow us to upload the image file, so its time to upload the reverse shell and get the connection back

For uploading reverse shell we need to do some of the minor changes in the burpsuit request like “rev.php” to “rev.jpg.php” and content-type also.
And we have successfully uploaded the reverse shell
4.) Capturing the Reverse Shell
For capturing the reverse shell I fired up my metasploit multi handler module to get the reverse shell


So here in this VM the kernel is vulnerable and fortunately we have the correct exploit in metasploit for this kernel to escalate our privilege.
5.) Privilege Escalation.
I found the exploit at “exploit/linux/local/bpf_sign_extension_priv_esc”

And after completing the required changes its time to run our exploit.
Hurray !!!!! ROOT


Our exploit worked successfully and we are root now. We got the root privilege and “flag.txt.txt” final flag too.
